Cloudflare OWASP ruleset: false positive on descriptions with shell snippets #124
Labels
No Label
Priority
Critical
Priority
High
Priority
Low
Priority
Normal
Reviewed
Confirmed
Reviewed
Duplicate
Reviewed
Invalid
Reviewed
Won't Fix
Status
Abandoned
Status
Blocked
Status
Need More Info
Type
Breaking
Type
Documentation
Type
Enhancement
Type
Feature
Type
Report
Type
Security
Type
Suggestion
Type
Testing
No Milestone
No project
No Assignees
2 Participants
Notifications
Due Date
No due date set.
Dependencies
No dependencies set.
Reference: infrastructure/extensions-website#124
Loading…
Reference in New Issue
Block a user
No description provided.
Delete Branch "%!s()"
Deleting a branch is permanent. Although the deleted branch may continue to exist for a short time before it actually gets removed, it CANNOT be undone in most cases. Continue?
When I tried to upload the extension's icon and featured image, Cloudflare blocked it.
Windows 11 Pro 22H2 22621.3527
Microsoft Edge 124.0.2478.97 (公式ビルド) (64 ビット)
Please refer to the attached video for network communication logs, etc.
CloudFlare blocks icon and featured image uploadsto Cloudflare blocks icon and featured image uploadsBy specifying an all-white image, the upload was successful. But I want to upload a meaningful image instead of this.
Thank you for a detailed report!
I've checked the CloudFlare (CF) ray-id in the logs, the request was blocked due to a total sum of CF managed rule flags:
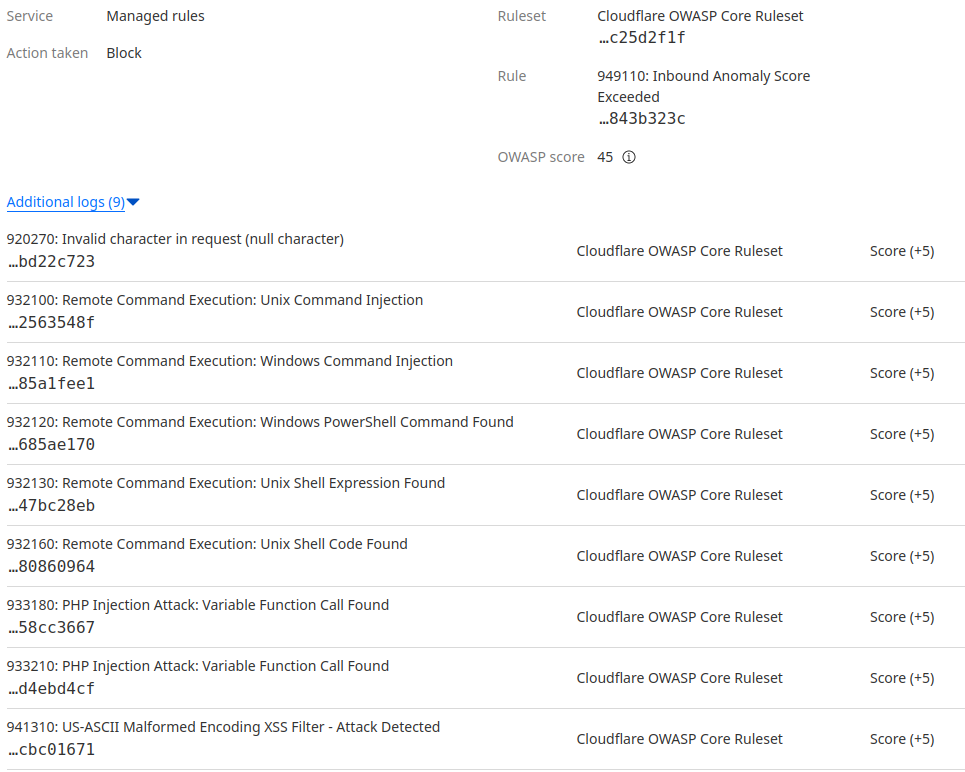
I have also checked if these rules are being triggered for other users, but in the last 72h only urls related to
vrmandvrm-extensionwere affected.Some of the triggered rules seem to refer to the shell commands present in the extension's description, but the fact that you could submit a different image with the same description makes me think that there may be something particular about the image binary payload.
Overall, I would prefer if we kept the CF rules in place, since I don't see them affecting other users.
May I ask you to try and re-upload the images after re-exporting them, possibly with a different image editor to change the binary payload? If you get blocked again, could you kindly share the ray-id?
Thank you for your detailed investigation. I created an icon using 4 different editors and uploaded it, and the results are shown below. please confirm.
By deleting the shell command listed in the extension details, I was able to successfully upload the image.
Thank you very much!
For research purposes, I've attached the description text of the extension that I originally posted.
Yes, I can see these ray ids in the logs, except for the first one.
Thank you for your patience!
I think that you (and other users) should be able to submit snippets with shell commands in the description, and these false positives in blocking are rather annoying.
I'll see if a more reasonable configuration is possible without disabling these rules entirely.
Cloudflare blocks icon and featured image uploadsto Cloudflare OWASP ruleset: false positive on descriptions with shell snippetsJust verified that the same combination of input (description text + any image) still leads to a blocked request.
I've tweaked the rules a little, but it wasn't enough, then I experimented with the description text, removing some parts, but keeping the shell snippets, and I managed to submit a form with a tweaked text and an image.
Also it appears that submitting a simple description (no markup) and images first, then editing the description should work, because it doesn't require to submit binary payloads and extensive markup in a single POST, and it helps to keep the cumulative WAF score lower, avoiding the block.
I will close this issue for now, since it's unlikely we will do more about this, unless more people complain.